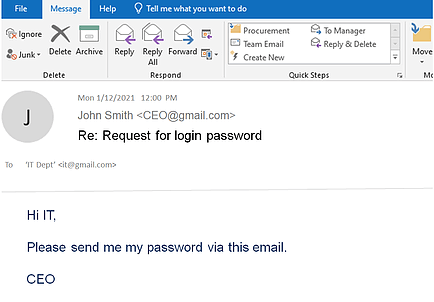
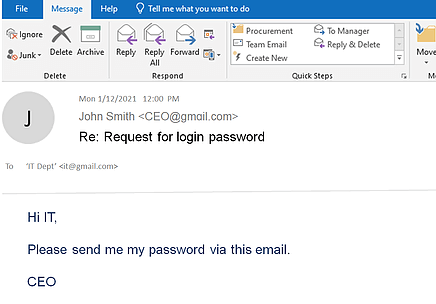
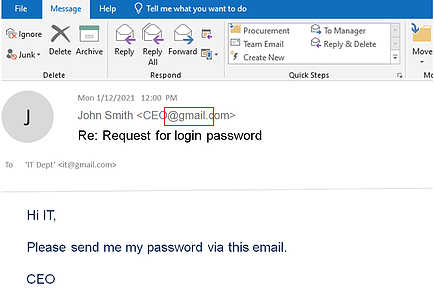
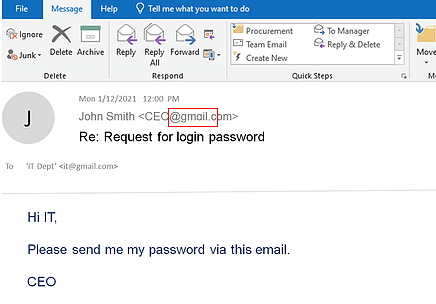
Cyber Attacks Are Evolving Every Day, Are You?
Criminals are learning new tricks every day, social engineering, CEO fraud, spear phishing. One user’s negligence will open a backdoor for cybercriminals. Do not take your chance when it comes to business data protection. Prevention is the top priority.